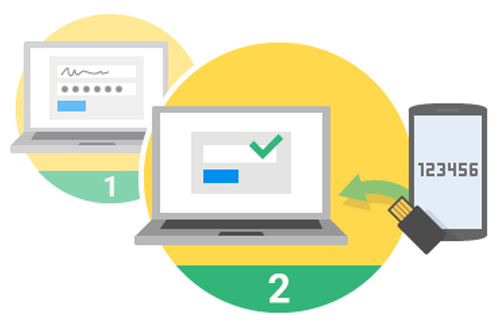
Have your accounts been compromised?
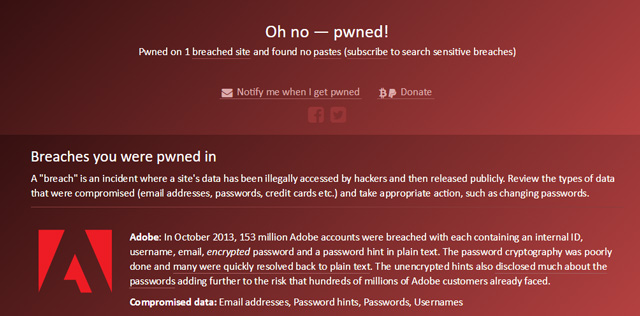
Over 189 websites have been compromised over the past few years leaking over 2 billion email accounts and their passwords. Since a lot of us end up using the same passwords for multiple accounts, these hacks can be very damaging. Once websites are hacked user’s passwords are made available to the world. So how do you know if your account has been compromised? There is a great site called haveibeenpwned. You can for free go to www.haveibeenpwned.com and enter your email address to see if any account tied to your email address has ever been part of any of these leaks. Find out if… Read moreHave your accounts been compromised?
 repair
repair at-home
at-home business
business about us
about us shop
shop off-site-backup
off-site-backup Get Apple Support
Get Apple Support